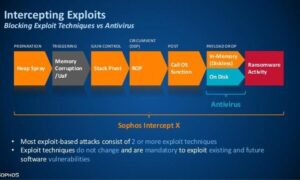
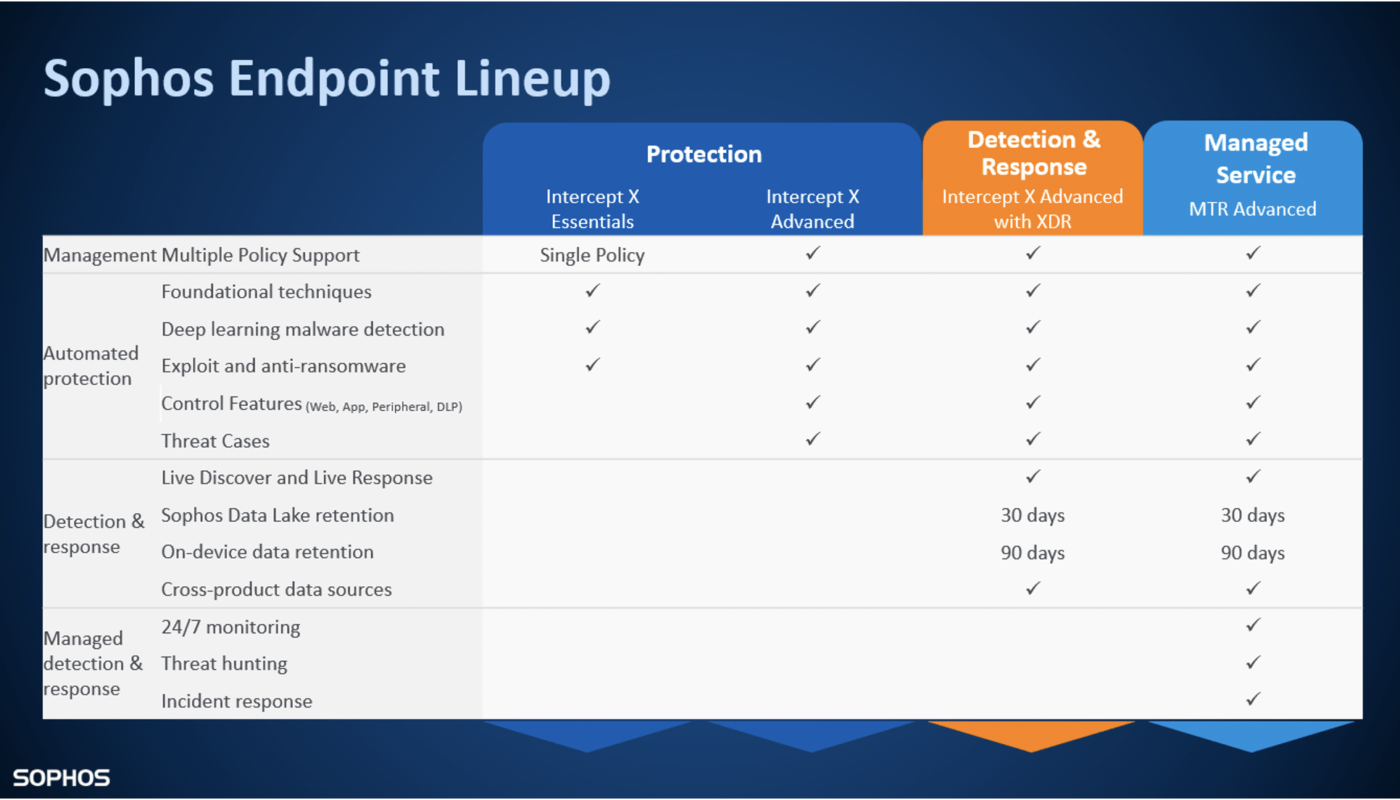
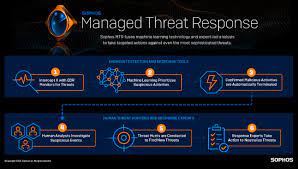
EndPoint With MTR/XDR Standard Services:
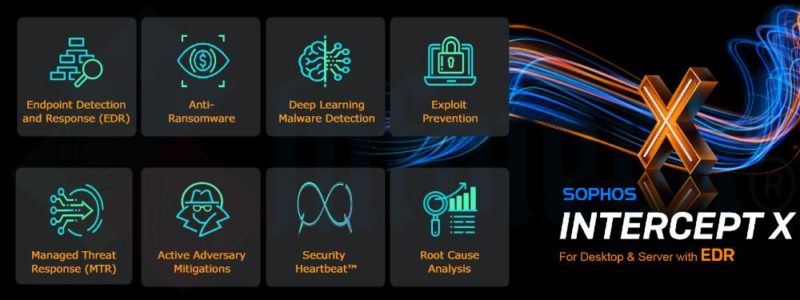
24/7 Lead Driven Threat Hunting: Confirmed malicious artifacts or activity (strong signals) are automatically blocked or terminated by our threat hunting system, freeing up our expert team to conduct lead-driven threat hunts. This proactive approach involves aggregating and investigating causal and adjacent events (weak signals) to uncover new Indicators of Attack (IoA) and Indicators of Compromise (IoC) that may have previously gone undetected.
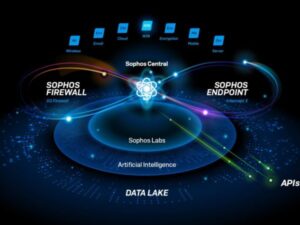
Security Health Check Systems: Ensure your Sophos Central products, starting with Intercept X Advanced with EDR, are operating at peak performance with our proactive security health check systems. We conduct thorough examinations of your operating conditions and recommend configuration improvements to enhance your security posture.
Activity Reporting: Receive comprehensive summaries of case activities to facilitate prioritization and communication within your team. Our detailed reports outline the threats detected and the response actions taken during each reporting period, empowering your team to stay informed and vigilant.
Adversarial Detections: Many successful cyber attacks leverage processes that can appear legitimate to traditional monitoring tools. Leveraging proprietary investigation techniques, our team distinguishes between legitimate behavior and the tactics, techniques, and procedures (TTPs) used by attackers, ensuring early detection and response to emerging threats.